The TRR-8 Tactical Radio Router
The TRR-8 Tactical Radio Router performs the functions of an IPv4/IPv6 network integrator. Integration and network-centricity have been achieved by equipping the device with a wide range of interfaces and telecommunications standards. TRR-8 integrates satellite terminals, WiFi wireless networks, 4G/5G operator networks, electrical and optical Ethernet networks. It integrates IPv4/IPv6, MPLS, MULTICAST and UNICAST traffic.
When developing the device, great emphasis was placed on the ease and user-friendliness of the configuration channels. The basic mode of operation is the ZEROcfg mode, where all activities performed so far by administrators and operators are carried out in automatic mode.
The device has a built-in desktop from which it is possible to set the device by calling the work scenario. The script in bulk programs all the necessary options. The preferred channel for remote configuration and monitoring is the web interface with an extensive help package in Polish. The WWW control concept allows you to configure the device from any military terminal equipped with an HTTPS browser, e.g. a smartphone, without the need to install specialized software.
The unique solutions used in the TRR-8 are:
- AutoWAN - a mechanism for automatically building the WAN structure of the wide area network with addressing. Connections are built in the FULLMESH mode without separate configuration servers which are always the sensitive points of the system;
- tunAKI - mechanism of automatic L3 tunnels built in FULLMESH mode;
- ARElink – mechanism of automatic addressless tunnels (L2) built in FULLMESH mode;
- OSPF/AC – automatic operating mode of the OSPF protocol. Automation applies to all parameters, including addressing. The mechanism works correctly with commercial and military routers and IPv4 satellite terminals;
- RAY - dynamic routing with reaction and reconstruction counted in single ms;
- ZEROloss - lossless transport mechanism in multipath systems
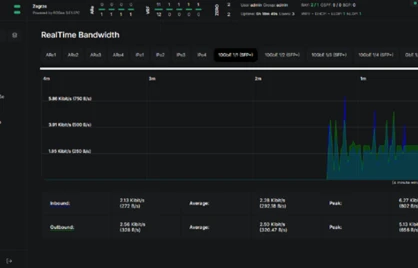
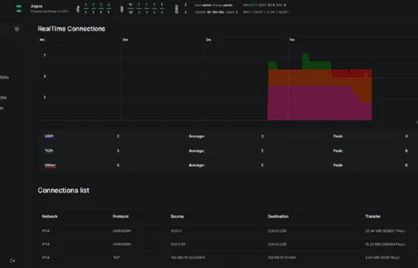
The device can monitor, analyze, filter traffic and record events about detected incidents. It has mechanisms that significantly limit the possibility of a DdoS attack. The device is designed to work as a black network router. The TRR8 router has implemented commercial encryption mechanisms, including AES256 and mechanisms with a minimum 2-level encryption cascade.
The TRR8 router uses the ZEROcfg mechanism is a concept of automatic device configuration that consists of many network solutions and standards. The technology is based on flat architecture, without central configuration and authorization servers. Establishing communication with the cooperating device (technology: radioline, streaming, packet, satellite, tropospheric, radio) takes place without the participation of the operator and without initial configuration of the device. Automatic configuration/reconfiguration of the device takes place through secure communication channels and each active device in the network undergoes an authorization process. Destroying a part of the working system automatically switches to alternative routes. The connection of a new device to the network is automatic.
The TRR8 router works as an independent field ICT node as well as an element of the ICT backbone being built for command posts. The TRR8 router, despite its revolutionary approach to the introduction of new technologies, remains fully compatible with communication systems operated by the Polish armed forces.
The TRR8 Tactical Radio Router has been equipped with the following interfaces and technologies:
- 10Gb/s optical interfaces with ZERO CFG technology;
- Optical interfaces led out on replaceable panels with ST, CTOS, MFM, LC connectors;
- Ethernet electrical interfaces resistant to overvoltage 4kV 10/700us in accordance with the requirement of ITU K.44
- ITU-T G8032 mechanism implementing hardware – Ethernet Ring Protection Switching (ERPS);
- WIFI 6e (AX) radio interfaces covering the band 2.4, 5 and the new 6..7 GHz band;
- Ultra sensitive 5G modems with directional antenna systems;
- Lossless data transport when changing the network topology (ZEROloss);
- Systems for transporting any data in automatically configured IP tunnels with cryptographic protection based on AES algorithm cascades;
- Automatically set tunnels in dedicated networks and the public Internet, also for devices connected via commercial GSM/LTE/5G modems (SKIPnat);
- Independent cryptography in L2/L3/L4 layers (MACsec, IPsec, VPN);
- SDN architecture "Virtual Router", "Virtual Switch";
- 7 x Ethernet RJ45F;
- Built-in operator panel for system monitoring and configuration.